[cryptography]
[schemes]
[protocols]
[implementations]
[authors]
Introduction to cryptography
The term "encryption" refers to the process in which data (which could represent text, voice, images, etc.) is temporarily coded into another type message, called ciphertext, which is unintelligible. A person or machine that holds possession of a specific piece information, called the decryption key, can carry out the inverse process of decryption of the ciphertext message. The purpose of the encryption process is obvious: to prevent malicious parties from gaining access to confidential information. As is explained later, encryption can also be used in implementing the following tasks:- proving message integrity (i.e. preventing malicious changes)
- authenticating the message sender
Symmetric or secret key encryption
In symmetric encryption the specific piece of information that is used in encrypting a message, the encryption key, is also the decryption key. The message sender and receiver both have the same key which they use to encrypt and decrypt messages.These algorithms are fast compared to asymmetric algorithms. The main problem is the key distribution. If symmetric encryption is used for example in encrypting an Internet session, the key cannot be delivered in this session because it could only be delivered as plain text. Therefore these algorithms are only used if the parties have some kind of prior relationship. Another problem is the key management: naturally a person should have a different key for each person he wants to communicate with.
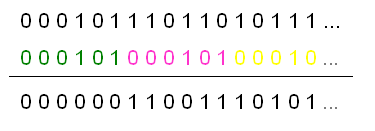
Figure: a simple scrambling with 6-bit key. (Source JI)
A simple example is shown above. Suppose that the message is coded into digital format e.g. by using the ASCII code. Every character (in case the message is text) could now consist of 7 bits. Suppose the key is a 6-bit long binary number. The cipher could then be obtained by XOR´ing the key with the message. Since the message is generally longer than 6 bits, the key is always re-used. Since XOR is its inverse operation, the receiver then again XOR´s the cipher with his key and as a result obtains the original message in ASCII code.
Asymmetric or public key encryption
In asymmetric encryption the encryption key and the decryption key are different. This enables one of the keys to be published while the other is kept in a secret place by the receiver. Both keys can be used in encrypting and decrypting messages but the point is that a message encrypted with one key, say the private key, can only be decrypted with the other key, in this case the public key. This property solves the problem of key distribution. In asymmetric encryption, when someone wants to send a secret message to someone else, the sender encrypts the message with the receiver´s public key. Consequently, the cipher can only be opened by the receiver, who holds possession to the corresponding private key.An important property of these algorithms from the viewpoint of user authentication is that if a message can be opened with someone´s public key, it can only have been encrypted with that person´s private key and a message that was encrypted with the public key can only be opened with the private key.
The most common of these algorithms is the RSA algorithm. It is several orders of magnitude slower than e.g. the symmetric DES. Another problem with these algorithms is authentication of the public keys. Digital certificates are used for this purpose.