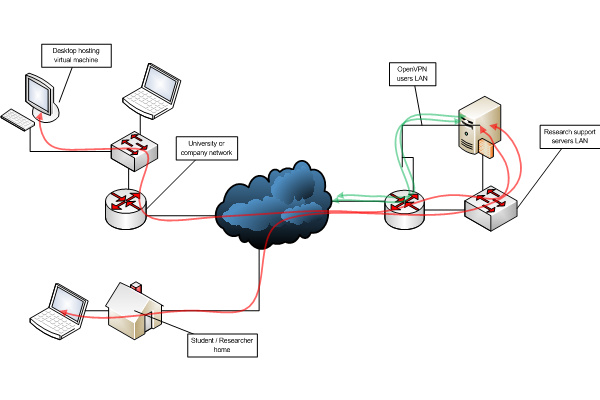
VPN for virtual machines allows rich networking to machines local to user even if local network infrasturcture does not support advanced networking. From user desktop a VPN tunnel is created and this tunnel has other end in research network supporting advanced networking features.
Research topics may require network access that is not possible within local network beacuse of network policy or because some networking technologies (like IPv6 or multicast) is not implemented. Although some research tasks could be run in remote machines, this is not a good solution for task related to video and other media.
By running a test environment in virtualised computer without access to local network it is possible to test experimental applications and services without putting security of campus network into risk.
This would provide possibilities to study advanced networking in student projects. In a typical home ADSL or cable modem access the service is just basic IPv4 without multicast and some services limited. If students are provided with access to research network, they would have a possibility to study advanced networking.
The solution will have three components:
For the researcher ("user") desktop computer a virtualisation software and OpenVPN client is installed. This can be done by support personnel, if required by organisation policy. The user logs into authentication server using Haka federated authentication and can download OpenVPN configuration files and certificate.
Using certificate provided, user can create OpenVPN connection to a OpenVPN server at resesarch networks and have provide her virtual machine a research network access.
It is possible that there exists multiple gateways in different networks that will make possible for a user to study e.g. multihoming.
There may be multiple user authentication servers or then one using federated authentication. The user needs to authenticate only once to get certificate. The lifetime of certificate is limited (6 months for students, a year for researchers). The certificate can be put on blacklist if terms of service in research network is violated.
LiveCD based image is available with following instructions.
To use federated authentication, user must be member of HAKA federation unless separate authentication (based on local or radius accounts) is established.

From picture the user authentication part (server and authentication infrastucture) is omited.
This work was supported by TEKES as part of the Future Internet program of TIVIT (Finnish Strategic Centre for Science, Technology and Innovation in the field of ICT).